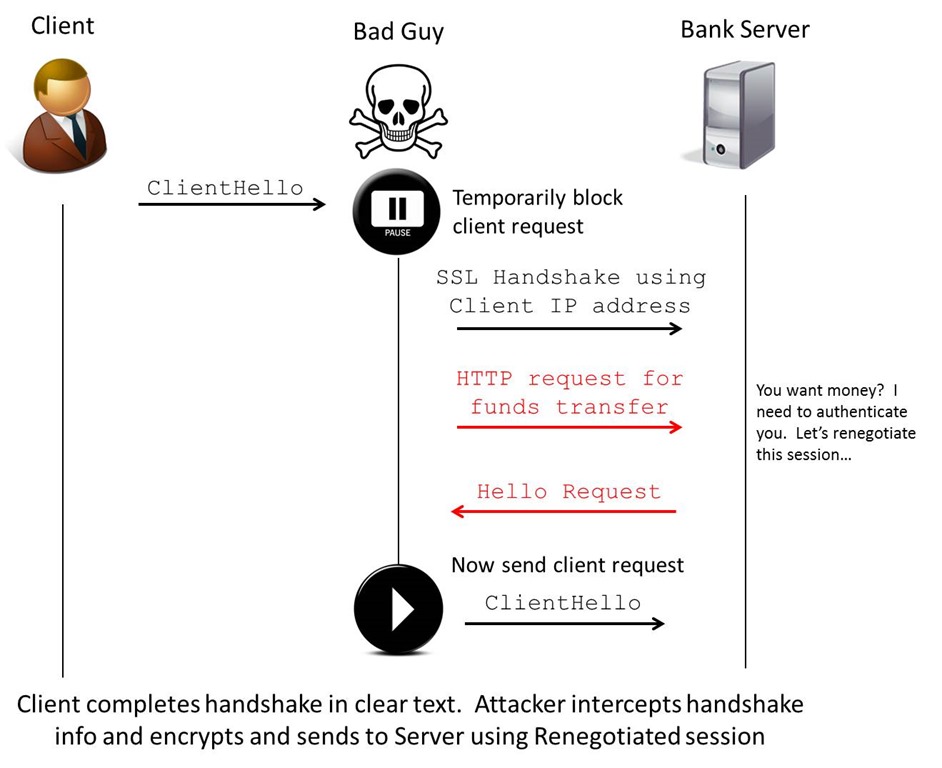
SSLv3 / TLS Man in the Middle vulnerability
Recently I have been looking into the vulnerabilities in the TLS negotiation process discovered late…

Ham Radio Iphone applications
I have a Iphone and have been loading Ham applications onto it… Below is a…
Hacking SCADA/SAS Systems Used Techniques, Known Incidents and Possible Mitigations
I have been working in the SCADA engineering, network design, project governance and security area…
Nmap Examples
Some Nmap examples I thought I would post. Scanning past Watchguard Firewalls: nmap -sS -iL…
How To Hijack Fast Food Drive-Thru Frequencies
This is an article I found on the Phone Losers site I thought I would…
Trojan software has been found in ATMs located in Eastern Europe
This is Great, I want one of these cards and a list of ATM’s. http://www.sophos.com/blogs/gc/g/2009/03/18/details-diebold-atm-trojan-horse-case/…
DUKPT Overview and Transaction notes
Hi, I was asked on another post relating to DUKPT to provide some backgound. Given…
VoIP and SIP links
I’m looking at the Microsoft OCS server and other SIP integration environments. So I thought…
