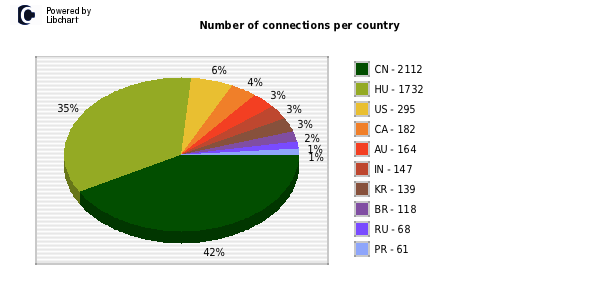
Honeypot Data Analysis
I’ve recently analysed a range of Honeypot data relating to about 3 months of malicious…
Next Generation SCADA Security: Best Practices and Client Puzzles
SCADA Presentation A cool document I thought I would share. It shows some good understanding…
WPA cracking is getting quicker
I was reading some posts on the Full-disclosure mailing list and came across the some…
How To Hijack Fast Food Drive-Thru Frequencies
This is an article I found on the Phone Losers site I thought I would…
Google Helps Find Webcam’s
The below lines can be placed into Google to find hidden cams on the net.…
Trojan software has been found in ATMs located in Eastern Europe
This is Great, I want one of these cards and a list of ATM’s. http://www.sophos.com/blogs/gc/g/2009/03/18/details-diebold-atm-trojan-horse-case/…
DUKPT Overview and Transaction notes
Hi, I was asked on another post relating to DUKPT to provide some backgound. Given…
SQL Injection Cheat Sheets
From Pentestmonkey.net, this is a great list of SQL Injection cheat sheets. Oracle MSSQL MySQL…

