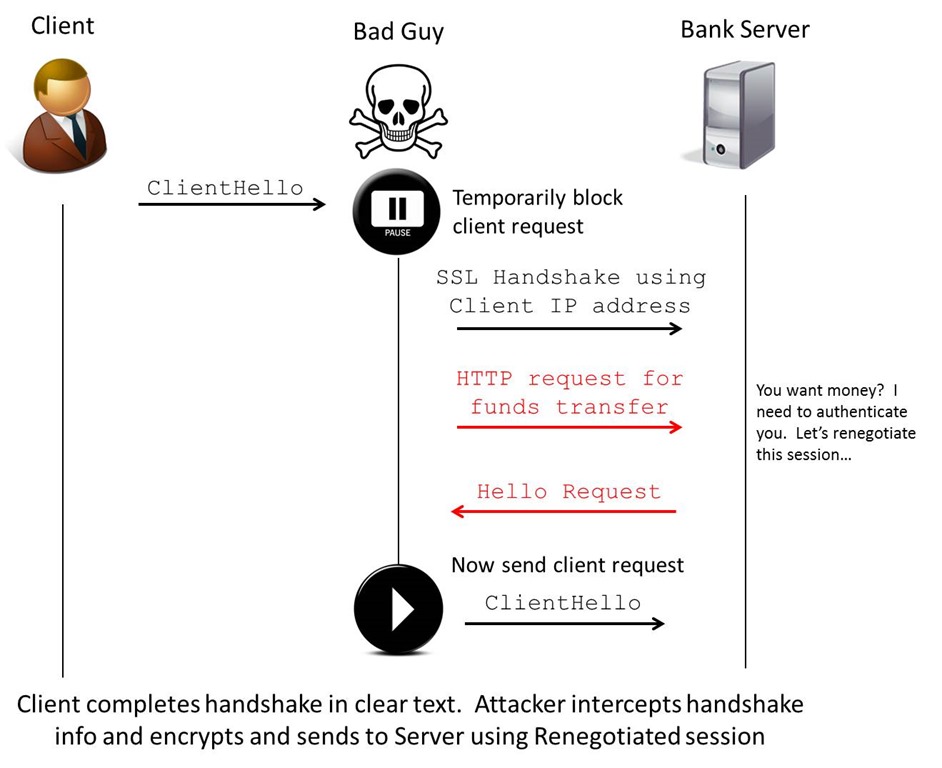
Recently I have been looking into the vulnerabilities in the TLS negotiation process discovered late last year.
There are a range of experts debating the exploit methods, tools and how it may be fixed (server or client site or both). From what I have seen so far this may prompt a change to the TLS standard to introduce an extension to the protocol to validate sessions (session hand off and certificate validity).
- The original description (site is suffering from a slashdot effect as I write this)
- The summary by the IETF TLSÂ workgroup, and promises for an amended protocol
- Marsh Ray’s paper
- March Ray’s protocol diagrams
www.win.tue.nl/hashclash/rogue-ca/
www.sslshopper.com/article-ssl-and-tls-renegotiation-vulnerability-discovered.html
I’m also trying to find some tools which may assist in testing for this. It looks like the exploit relies on an ARP poison or similar and then inserting plain text into the negotiation process.
Could be something that can be fixed over time as servers and clients are patched.
Leave a Reply