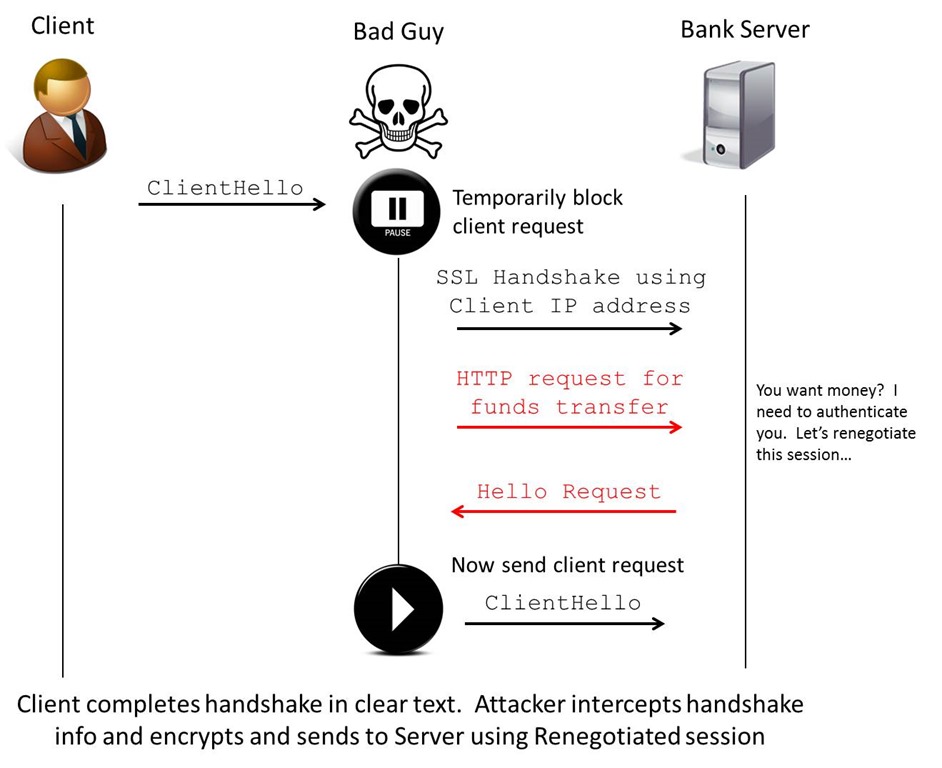
SSLv3 / TLS Man in the Middle vulnerability
Recently I have been looking into the vulnerabilities in the TLS negotiation process discovered late…
SCADA Security Presentation
This is a presentation I gave on SCADA security some time ago. It was originally…
Hacking SCADA/SAS Systems Used Techniques, Known Incidents and Possible Mitigations
I have been working in the SCADA engineering, network design, project governance and security area…
Next Generation SCADA Security: Best Practices and Client Puzzles
SCADA Presentation A cool document I thought I would share. It shows some good understanding…
SCADA considerations
Procedures Corporate Information Protection Security Management Information Classification Physical (and Environmental) Security Personnel Security Security…
Nmap Examples
Some Nmap examples I thought I would post. Scanning past Watchguard Firewalls: nmap -sS -iL…
WPA cracking is getting quicker
I was reading some posts on the Full-disclosure mailing list and came across the some…

