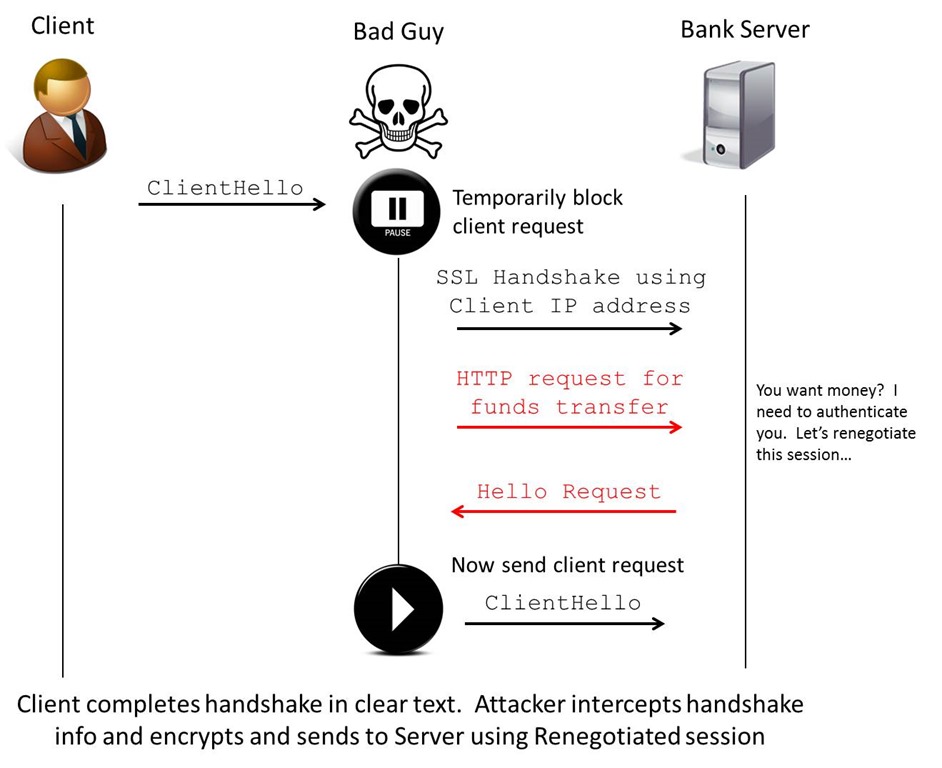
SSLv3 / TLS Man in the Middle vulnerability
Recently I have been looking into the vulnerabilities in the TLS negotiation process discovered late…
Nmap Examples
Some Nmap examples I thought I would post. Scanning past Watchguard Firewalls: nmap -sS -iL…
Google Helps Find Webcam’s
The below lines can be placed into Google to find hidden cams on the net.…
DUKPT Overview and Transaction notes
Hi, I was asked on another post relating to DUKPT to provide some backgound. Given…
Secure Application Development links
Hi, I have been putting some secure application development documents together recently and have found…
Internet Banking Security Assessment Considerations
I was asked some time ago to provide a list of things which may be…

