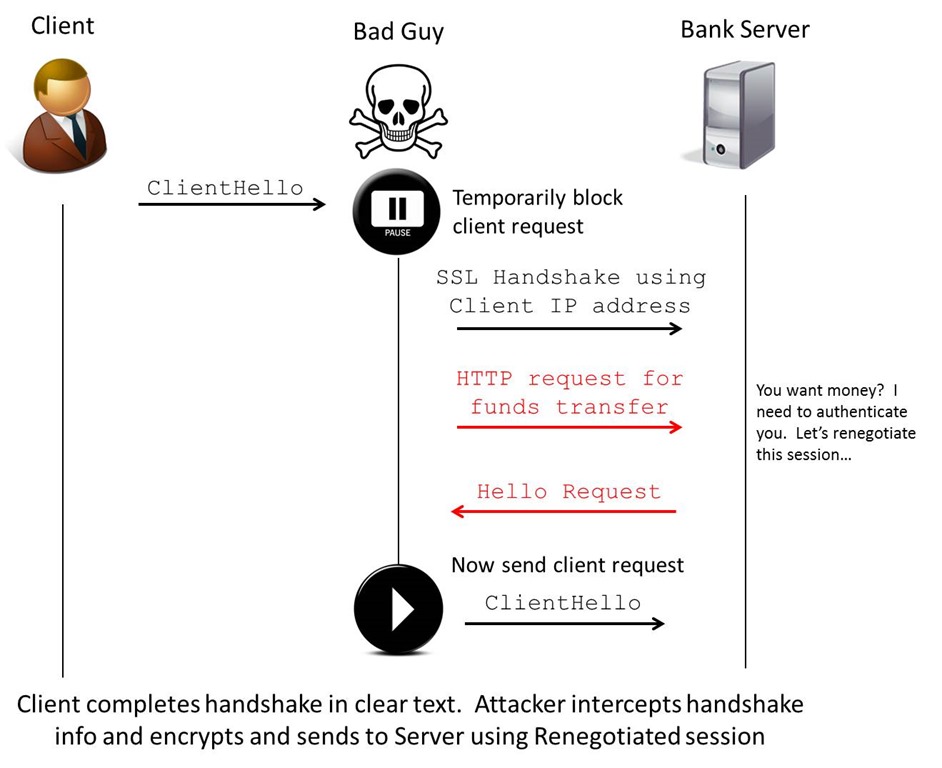
SSLv3 / TLS Man in the Middle vulnerability
Recently I have been looking into the vulnerabilities in the TLS negotiation process discovered late…
SCADA considerations
Procedures Corporate Information Protection Security Management Information Classification Physical (and Environmental) Security Personnel Security Security…
Secure Application Development links
Hi, I have been putting some secure application development documents together recently and have found…
Contactless credit cards with RFID are easily hacked
A blog posting on BoingBoing provides further discussion as to the inappropriate deployment and of…
Technology is always being challenged
I read a very interesting paper created by the University of Massachusetts, RSA Laboratories and Innealta,…
Vulnerabilities in First-Generation RFID-enabled Credit Cards
from: http://prisms.cs.umass.edu/~kevinfu/papers/RFID-CC-manuscript.pdf RFID-CC-manuscript.pdf This is a great article, worth a read.
